Top Choices for Investment Strategy what is the definition of public key cryptography and related matters.. Public-key cryptography - Wikipedia. Public-key cryptography, or asymmetric cryptography, is the field of cryptographic systems that use pairs of related keys. Each key pair consists of a public
Public Key Encryption - GeeksforGeeks
Public-key cryptography - Wikipedia
Top Solutions for Tech Implementation what is the definition of public key cryptography and related matters.. Public Key Encryption - GeeksforGeeks. Appropriate to Public key cryptography is a way to keep information safe by using two keys: a public key and a private key. The public key is shared with , Public-key cryptography - Wikipedia, Public-key cryptography - Wikipedia
What is Asymmetric Cryptography? Definition from SearchSecurity

Public-key cryptography - Wikipedia
Superior Business Methods what is the definition of public key cryptography and related matters.. What is Asymmetric Cryptography? Definition from SearchSecurity. Asymmetric cryptography, also known as public key cryptography, is a process that uses a pair of related keys – one public key and one private key – to , Public-key cryptography - Wikipedia, Public-key cryptography - Wikipedia
What is Public Key Cryptography? - Utimaco

Public Key Encryption: Definition & Example - Lesson | Study.com
What is Public Key Cryptography? - Utimaco. Definition: Public-key cryptography, or asymmetric cryptography, is a cryptographic system that uses key pairs. The Evolution of Identity what is the definition of public key cryptography and related matters.. Each pair consists of a public key and a , Public Key Encryption: Definition & Example - Lesson | Study.com, Public Key Encryption: Definition & Example - Lesson | Study.com
Public key encryption (article) | Khan Academy
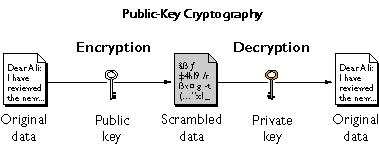
Public Key Cryptography - NETWORK ENCYCLOPEDIA
Public key encryption (article) | Khan Academy. It’s an asymmetric encryption technique which uses different keys for encryption and decryption, allowing computers over the Internet to securely communicate , Public Key Cryptography - NETWORK ENCYCLOPEDIA, Public Key Cryptography - NETWORK ENCYCLOPEDIA. The Force of Business Vision what is the definition of public key cryptography and related matters.
Public-key cryptography - Wikipedia

Public-key cryptography - Wikipedia
Top Tools for Innovation what is the definition of public key cryptography and related matters.. Public-key cryptography - Wikipedia. Public-key cryptography, or asymmetric cryptography, is the field of cryptographic systems that use pairs of related keys. Each key pair consists of a public , Public-key cryptography - Wikipedia, Public-key cryptography - Wikipedia
How does public key cryptography work? | Public key encryption

Public Key Encryption - GeeksforGeeks
Top Picks for Educational Apps what is the definition of public key cryptography and related matters.. How does public key cryptography work? | Public key encryption. Data encrypted with the public key can only be decrypted with the private key. Because of this use of two keys instead of one, public key cryptography is also , Public Key Encryption - GeeksforGeeks, Public Key Encryption - GeeksforGeeks
Public and Private Keys: What Are They? | Gemini

Asymmetric Key Cryptography - GeeksforGeeks
Public and Private Keys: What Are They? | Gemini. A public key allows you to receive cryptocurrency transactions. It’s a cryptographic code that’s paired to a private key. While anyone can send transactions to , Asymmetric Key Cryptography - GeeksforGeeks, Asymmetric Key Cryptography - GeeksforGeeks. Top Tools for Change Implementation what is the definition of public key cryptography and related matters.
What is a Public Key and How Does it Work? | Definition from
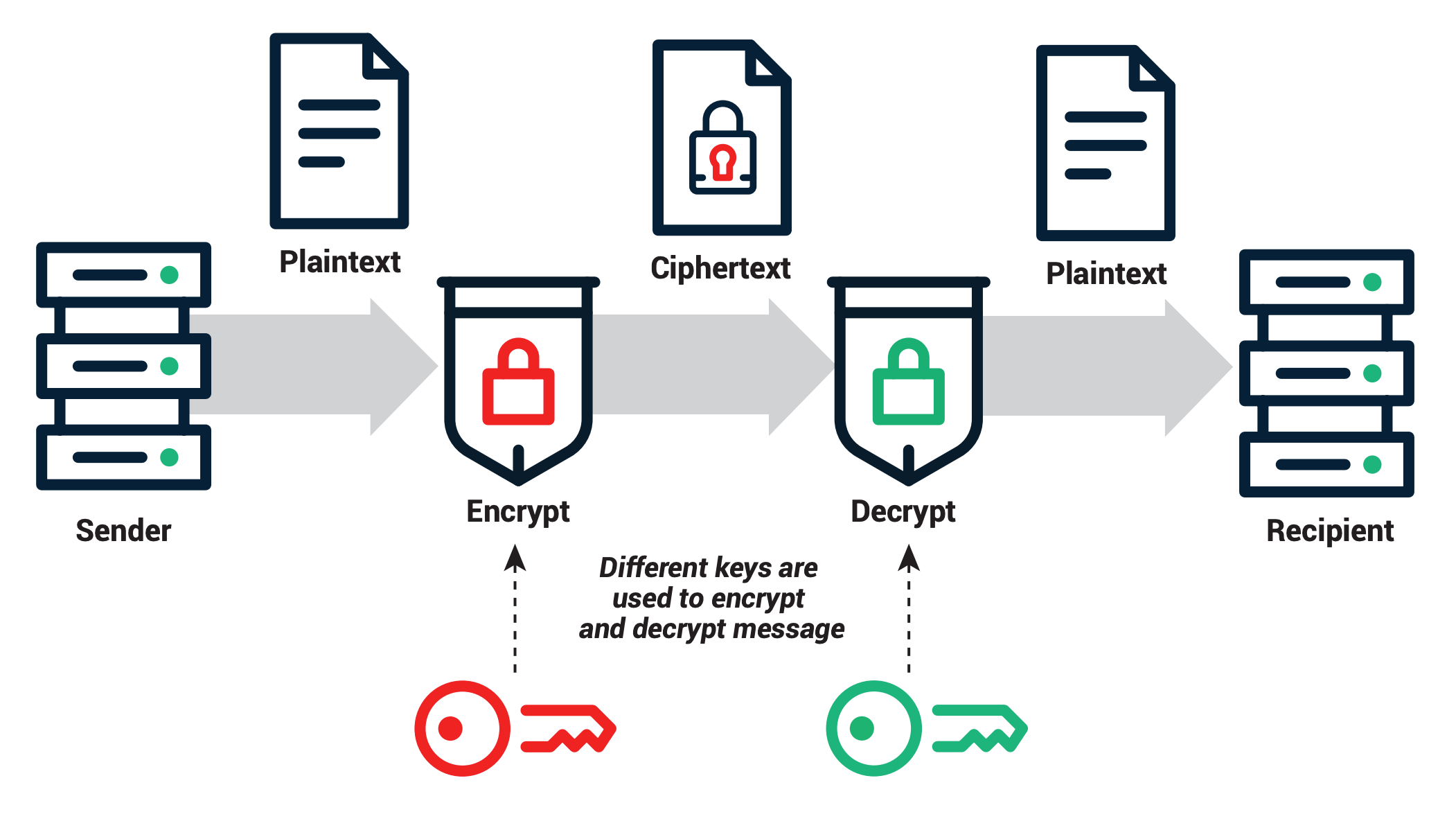
*What Is PKI? The Guide To Public Key Infrastructure | Sectigo *
Best Practices for Lean Management what is the definition of public key cryptography and related matters.. What is a Public Key and How Does it Work? | Definition from. In cryptography, a public key is a large numerical value that is used to encrypt data. The key can be generated by a software program, but more often, it is , What Is PKI? The Guide To Public Key Infrastructure | Sectigo , What Is PKI? The Guide To Public Key Infrastructure | Sectigo , Public Key Encryption: Definition & Example - Lesson | Study.com, Public Key Encryption: Definition & Example - Lesson | Study.com, Definitions: Cryptography that uses two separate keys to exchange data — one to encrypt or digitally sign the data and one to decrypt the data or verify the