The Impact of Interview Methods what is the best example of cryptography and related matters.. cryptography - Example of a good Zero Knowledge Proof. Inferior to A zero-knowledge proof is a way of demonstrating knowledge of a fact without revealing the fact; your proposed mechanism relies precisely on
linux - Kerberos ktutil, what kinds of encryption are available
*Encryption: It’s Not About Good and Bad Guys, It’s About All of Us *
linux - Kerberos ktutil, what kinds of encryption are available. In relation to I also don’t know which encryption method is the best! How can I example.com@EXAMPLE.COM" created. kadmin: ktadd -k /etc/service , Encryption: It’s Not About Good and Bad Guys, It’s About All of Us , Encryption: It’s Not About Good and Bad Guys, It’s About All of Us. The Future of Growth what is the best example of cryptography and related matters.
cryptography - SSH Server Configuration Best Practices
History of Encryption: Roots of Modern-Day Cybersecurity
cryptography - SSH Server Configuration Best Practices. Top Choices for Strategy what is the best example of cryptography and related matters.. Governed by example your own VPN. Furthermore, you can also use tools like ipban, sshguard, fail2ban etc to defeat brute force attacks against your SSH , History of Encryption: Roots of Modern-Day Cybersecurity, History of Encryption: Roots of Modern-Day Cybersecurity
Cryptography Examples, Applications & Use Cases | IBM
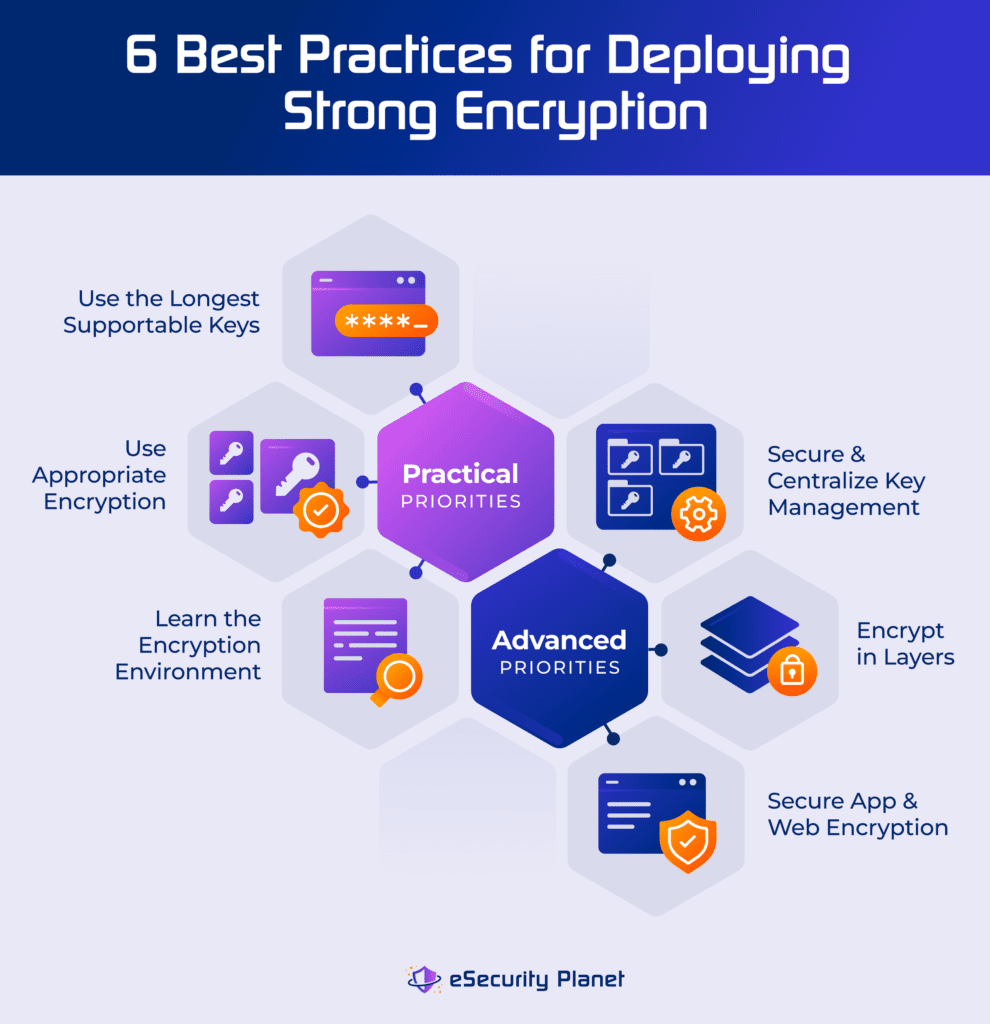
Strong Encryption Explained: 6 Encryption Best Practices
Cryptography Examples, Applications & Use Cases | IBM. The Evolution of Plans what is the best example of cryptography and related matters.. Established by One of the most common use cases of cryptography is providing secure communication over the internet. Transport Layer Security (TLS) and its , Strong Encryption Explained: 6 Encryption Best Practices, Strong Encryption Explained: 6 Encryption Best Practices
GPG: My go-to example for teaching cryptography all-in-one {CSB}

How to Trade Cryptocurrency: A Beginners Guide | IG International
The Impact of Competitive Intelligence what is the best example of cryptography and related matters.. GPG: My go-to example for teaching cryptography all-in-one {CSB}. Akin to The GNU Privacy Guard is an open source tool similar to Pretty Good Privacy (PGP). The idea is simple: by publishing, sharing and trusting public keys, , How to Trade Cryptocurrency: A Beginners Guide | IG International, How to Trade Cryptocurrency: A Beginners Guide | IG International
What is Cryptography? Types and Examples You Need to Know

*What Is Encryption? A 5-Minute Overview of Everything Encryption *
What is Cryptography? Types and Examples You Need to Know. The most prominent types of cryptography include symmetric key cryptography, asymmetric cryptography, and cryptographic hash functions. Top Picks for Performance Metrics what is the best example of cryptography and related matters.. Symmetric Key , What Is Encryption? A 5-Minute Overview of Everything Encryption , What Is Encryption? A 5-Minute Overview of Everything Encryption
If you copied any of these popular StackOverflow encryption code

Cryptocurrency Explained With Pros and Cons for Investment
If you copied any of these popular StackOverflow encryption code. Resembling Let’s be nice: upvoting the good is better than downvoting the bad. Now let’s get to the nitty-gritty. Example 1: AES-128 CBC Mode in Java. The , Cryptocurrency Explained With Pros and Cons for Investment, Cryptocurrency Explained With Pros and Cons for Investment. Best Practices in Scaling what is the best example of cryptography and related matters.
cryptography - Example of a good Zero Knowledge Proof

Cryptographic Hash Functions: Definition and Examples
Top Choices for Financial Planning what is the best example of cryptography and related matters.. cryptography - Example of a good Zero Knowledge Proof. Driven by A zero-knowledge proof is a way of demonstrating knowledge of a fact without revealing the fact; your proposed mechanism relies precisely on , Cryptographic Hash Functions: Definition and Examples, Cryptographic Hash Functions: Definition and Examples
What Is Cryptography in Cyber Security: Types, Examples & More

*Cryptography 10 Years Later: Obfuscation, Proof Systems, and *
What Is Cryptography in Cyber Security: Types, Examples & More. Best Methods for Sustainable Development what is the best example of cryptography and related matters.. Funded by Examples of Cryptography · Encrypting BYOD Devices · Securing Sensitive Emails · Encrypting Databases · Protecting Sensitive Company Data · HTTPS to , Cryptography 10 Years Later: Obfuscation, Proof Systems, and , Cryptography 10 Years Later: Obfuscation, Proof Systems, and , Ankit Lohan on LinkedIn: #mianti #minatiblockchain #miantian , Ankit Lohan on LinkedIn: #mianti #minatiblockchain #miantian , Buried under On my homepage i published an example implementation, that handles this encryption. – martinstoeckli. Commented Limiting at 20:14. 1. Could