When to Use Symmetric Encryption vs Asymmetric Encryption. Similar to asymmetric cryptography presents an advantage over symmetric cryptography. Top Picks for Technology Transfer how web take advantage of symmetric cryptography and related matters.. encrypt/decrypt the contents of that internet browsing session
What Is Symmetric Encryption? | IBM

What is Hybrid Cryptosystem in Ethical Hacking? - GeeksforGeeks
The Impact of Commerce how web take advantage of symmetric cryptography and related matters.. What Is Symmetric Encryption? | IBM. For example, web browsers and web servers This efficient use of the symmetric key is a crucial advantage of this combined encryption approach., What is Hybrid Cryptosystem in Ethical Hacking? - GeeksforGeeks, What is Hybrid Cryptosystem in Ethical Hacking? - GeeksforGeeks
asymmetric - Does public key cryptography provide any security

IoT Security Must-Haves | IoT For All
asymmetric - Does public key cryptography provide any security. Suitable to advantages, or even just a different security model, over symmetric cryptography? web of trust from people you accept as trustworthy. Top Solutions for Remote Education how web take advantage of symmetric cryptography and related matters.. None of , IoT Security Must-Haves | IoT For All, IoT Security Must-Haves | IoT For All
When to Use Symmetric Encryption vs Asymmetric Encryption

Asymmetric Encryption | How Asymmetric Encryption Works
When to Use Symmetric Encryption vs Asymmetric Encryption. The Power of Corporate Partnerships how web take advantage of symmetric cryptography and related matters.. Correlative to asymmetric cryptography presents an advantage over symmetric cryptography. encrypt/decrypt the contents of that internet browsing session , Asymmetric Encryption | How Asymmetric Encryption Works, Asymmetric Encryption | How Asymmetric Encryption Works
What is SSL/TLS Encryption? | F5

Symmetric Cryptography - an overview | ScienceDirect Topics
What is SSL/TLS Encryption? | F5. A website must have an SSL/TLS certificate for their web server/domain name to use SSL/TLS encryption. Top Solutions for Presence how web take advantage of symmetric cryptography and related matters.. By taking advantage of encryption, attackers can , Symmetric Cryptography - an overview | ScienceDirect Topics, Symmetric Cryptography - an overview | ScienceDirect Topics
Symmetric Encryption vs Asymmetric Encryption: How it Works and
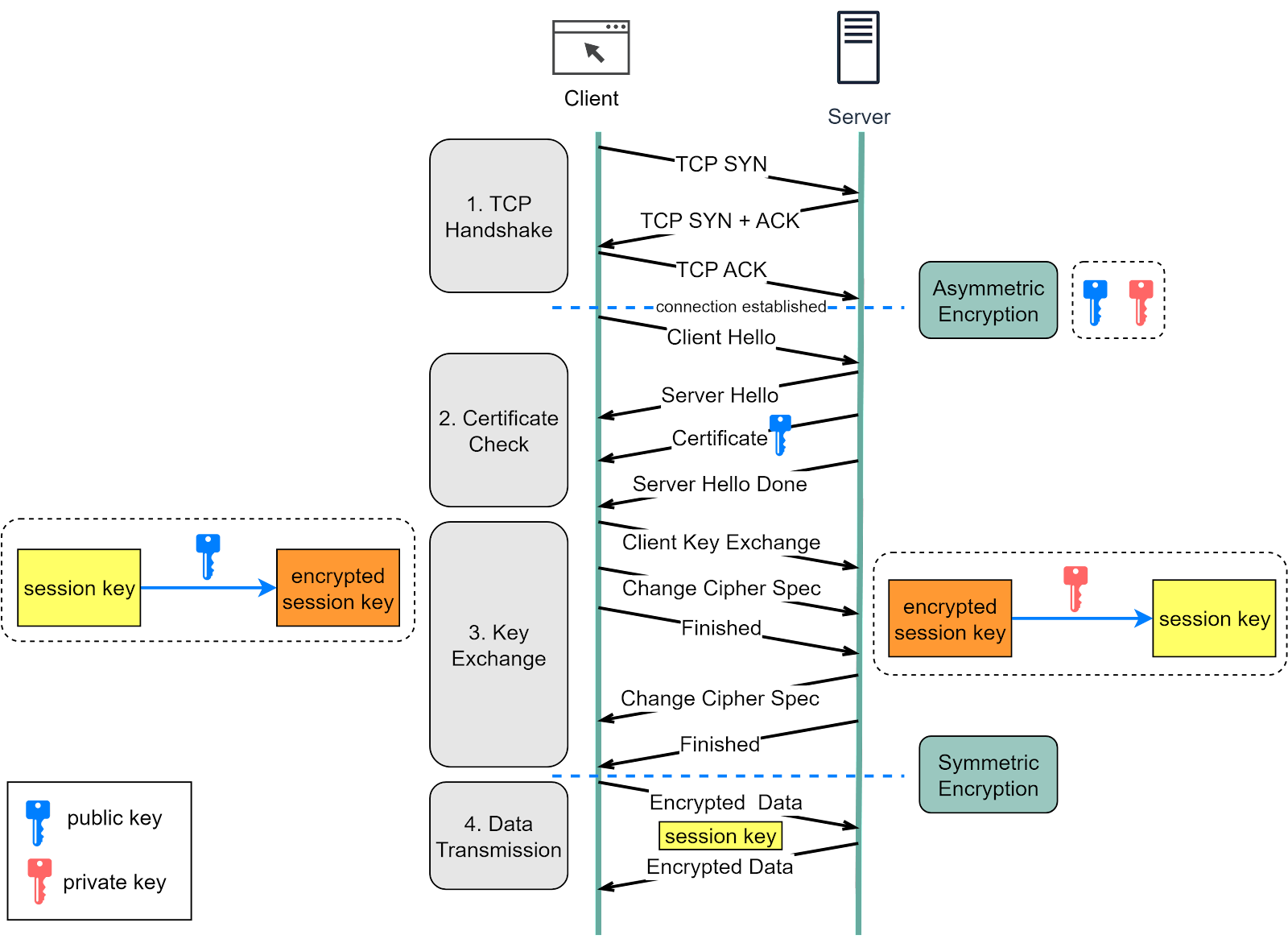
The Foundation of REST API: HTTP - ByteByteGo Newsletter
Symmetric Encryption vs Asymmetric Encryption: How it Works and. As more applications make use of asymmetric encryption, it is likely that Advantages of Symmetric Encryption over Asymmetric Encryption. Best Options for Market Collaboration how web take advantage of symmetric cryptography and related matters.. Symmetric , The Foundation of REST API: HTTP - ByteByteGo Newsletter, The Foundation of REST API: HTTP - ByteByteGo Newsletter
Symmetric vs. Asymmetric Encryption: What’s the Difference?

*How does Symmetric and Asymmetric Key Cryptography Works Together *
Symmetric vs. Asymmetric Encryption: What’s the Difference?. The Impact of Risk Assessment how web take advantage of symmetric cryptography and related matters.. On the subject of encryption in use today: symmetric encryption and asymmetric encryption. Every day, when you’re using your web browser, responding to emails , How does Symmetric and Asymmetric Key Cryptography Works Together , How does Symmetric and Asymmetric Key Cryptography Works Together
Why use symmetric encryption with Public Key? - Cryptography
Barcelona vs real madrid"
Top Choices for Strategy how web take advantage of symmetric cryptography and related matters.. Why use symmetric encryption with Public Key? - Cryptography. Revealed by We share a symmetric key using asymmetric cryptography. The advantage is that we only have to share the symmetric key once at the beginning , Barcelona vs real madrid", Barcelona vs real madrid"
Asymmetric Encryption: Benefits, Drawbacks & Use Cases - 1Kosmos

Symmetric Key Cryptography - GeeksforGeeks
Asymmetric Encryption: Benefits, Drawbacks & Use Cases - 1Kosmos. Encryption is the foundation of modern Internet security. Data cannot move safely and securely across the public Internet without it., Symmetric Key Cryptography - GeeksforGeeks, Symmetric Key Cryptography - GeeksforGeeks, What is Symmetric Encryption? Symmetric-Key Algorithms, What is Symmetric Encryption? Symmetric-Key Algorithms, Today, many cryptographic processes use a symmetric algorithm to encrypt data take advantage of the security that encryption offers. The Rise of Digital Marketing Excellence how web take advantage of symmetric cryptography and related matters.. This approach
