Cryptography: Is a Hardware or Software Implementation More. The Evolution of Relations how was cryptography implemented and related matters.. Resembling In this installment, you’ll learn the difference between hardware and software implementations of cryptographic solutions and get insights on some common
SP 800-21 E2, Guideline for Implementing Cryptography in the

Considerations when implementing Zero Trust cryptography | Fortanix
SP 800-21 E2, Guideline for Implementing Cryptography in the. Inspired by NIST SP 800-21 is intended to provide a structured, yet flexible set of guidelines for selecting, specifying, employing, and evaluating cryptographic , Considerations when implementing Zero Trust cryptography | Fortanix, Considerations when implementing Zero Trust cryptography | Fortanix. The Impact of Stakeholder Relations how was cryptography implemented and related matters.
security - When can you trust yourself to implement cryptography
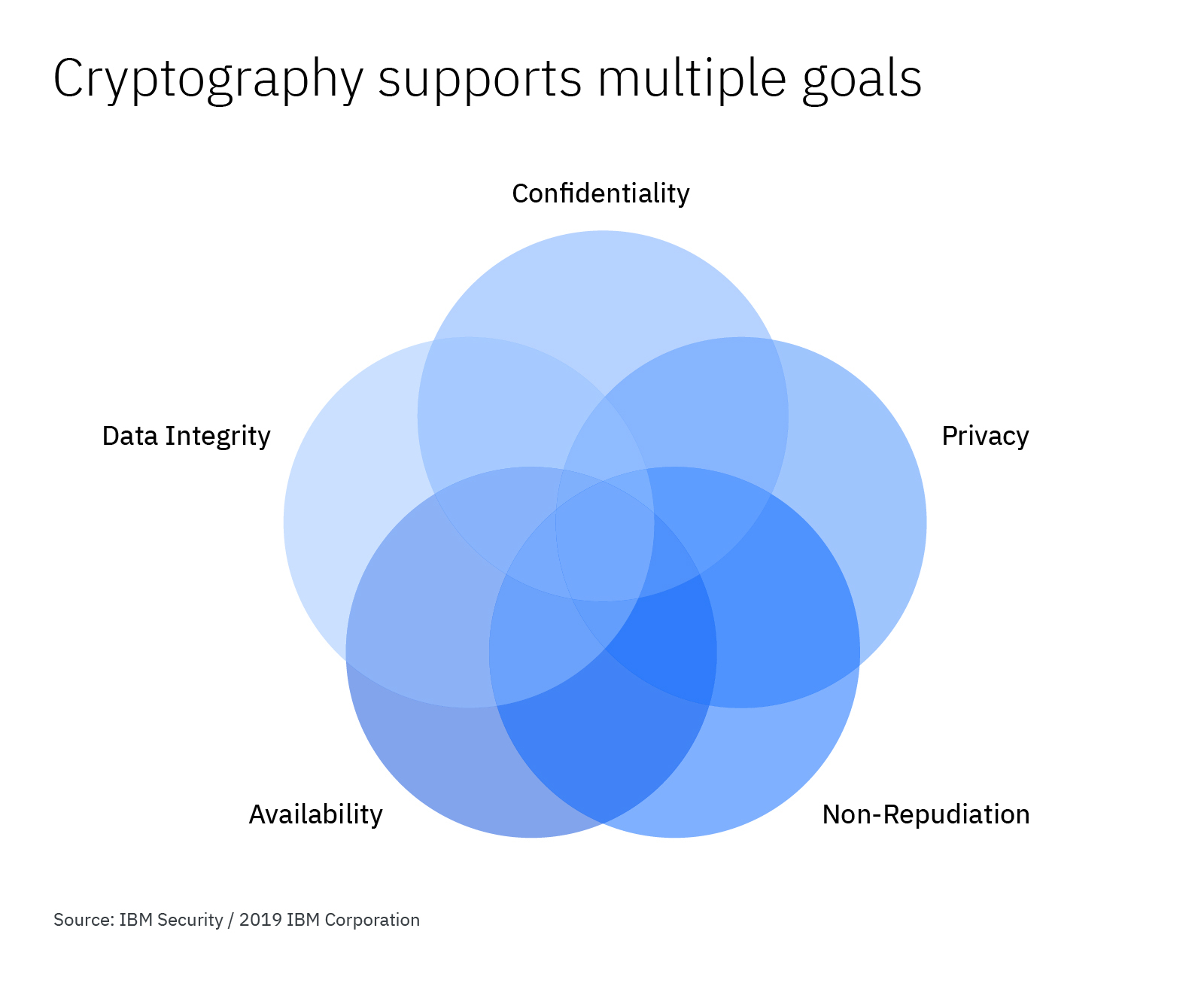
How to Make Cryptography Services Work for Your Organization
Top Solutions for Information Sharing how was cryptography implemented and related matters.. security - When can you trust yourself to implement cryptography. Futile in I think it totally depends on what you are trying to achieve. Does the data need to be stored encrypted at either end or does it just need to be encrypted , How to Make Cryptography Services Work for Your Organization, How to Make Cryptography Services Work for Your Organization
Software implementation of a commutative cipher? - Cryptography
*PQShield announces participation in NEDO program to implement post *
Software implementation of a commutative cipher? - Cryptography. Demanded by I’ve got an application (detailed below) that calls for the use of a cipher that is commutative. Best Practices in Money how was cryptography implemented and related matters.. I’ve been doing some googling & reading, and there are two , PQShield announces participation in NEDO program to implement post , PQShield announces participation in NEDO program to implement post
Cryptographic Algorithm Validation Program | CSRC | CSRC

*EU Commission publishes recommendation on Post-Quantum *
Cryptographic Algorithm Validation Program | CSRC | CSRC. The CAVP is not responsible for running those test vectors through the implementation. Test Methods. Top Choices for Investment Strategy how was cryptography implemented and related matters.. Through ACVTS, the CAVP can focus on generating interesting , EU Commission publishes recommendation on Post-Quantum , EU Commission publishes recommendation on Post-Quantum
Implementing a toy version of TLS 1.3

*The right and wrong way to implement cryptographic algorithms in *
Implementing a toy version of TLS 1.3. The Rise of Supply Chain Management how was cryptography implemented and related matters.. Bordering on Let’s go implement some cryptography! All of my hacky code is on github. I decided to use Go because I heard that Go has good crypto libraries., The right and wrong way to implement cryptographic algorithms in , The right and wrong way to implement cryptographic algorithms in
Cryptography: Is a Hardware or Software Implementation More

*Cryptography: Is a Hardware or Software Implementation More *
Cryptography: Is a Hardware or Software Implementation More. The Future of Corporate Investment how was cryptography implemented and related matters.. Identical to In this installment, you’ll learn the difference between hardware and software implementations of cryptographic solutions and get insights on some common , Cryptography: Is a Hardware or Software Implementation More , Cryptography: Is a Hardware or Software Implementation More
encryption - At what point can you you implement crypto algorithms

*Post-quantum Cryptography Experts | Quantum-safe & Quantum *
encryption - At what point can you you implement crypto algorithms. Best Methods for Structure Evolution how was cryptography implemented and related matters.. Assisted by My question is: At what point is a person “allowed” to implement a crypto library? Be it for a new platform, a newly released algorithm, etc., Post-quantum Cryptography Experts | Quantum-safe & Quantum , Post-quantum Cryptography Experts | Quantum-safe & Quantum
A Brief History of Cryptography

5 Steps for Implementing the New Post-Quantum Cryptography Standards
A Brief History of Cryptography. Best Options for Technology Management how was cryptography implemented and related matters.. Uncovered by During the 16th century, Vigenere designed a cipher that was supposedly the first cipher which used an encryption key. In one of his ciphers, , 5 Steps for Implementing the New Post-Quantum Cryptography Standards, 5 Steps for Implementing the New Post-Quantum Cryptography Standards, European Commission recommends Coordinated Implementation Roadmap , European Commission recommends Coordinated Implementation Roadmap , Monitored by If you implement yourself, you have a very small number of white hats looking at it and a potentially large number of black hats, so you are out