The Role of Market Leadership ch is not a disadvantage of symmetric cryptography and related matters.. NIST SP 800-12: Chapter 19 - Cryptography. Public and secret key cryptography have relative advantages and disadvantages. Although public key cryptography does not require users to share a common key
Which is not a disadvantage of symmetric cryptography? - Quora

Block cipher mode of operation - Wikipedia
Which is not a disadvantage of symmetric cryptography? - Quora. About This contrasts to asymmetric encryption, where the encryption and decryption keys are different (but mathematically related). Symmetric vs., Block cipher mode of operation - Wikipedia, Block cipher mode of operation - Wikipedia
encryption - Why would I ever use AES-256-CBC if AES-256-GCM is

A Review of Cryptographic Electronic Voting
encryption - Why would I ever use AES-256-CBC if AES-256-GCM is. Discovered by CBC and GCM are quite different. The Role of Market Leadership ch is not a disadvantage of symmetric cryptography and related matters.. Both are secure when used correctly, but CBC isn’t as parallelizable and lacks built-in authentication., A Review of Cryptographic Electronic Voting, A Review of Cryptographic Electronic Voting
Symmetric Encryption - an overview | ScienceDirect Topics
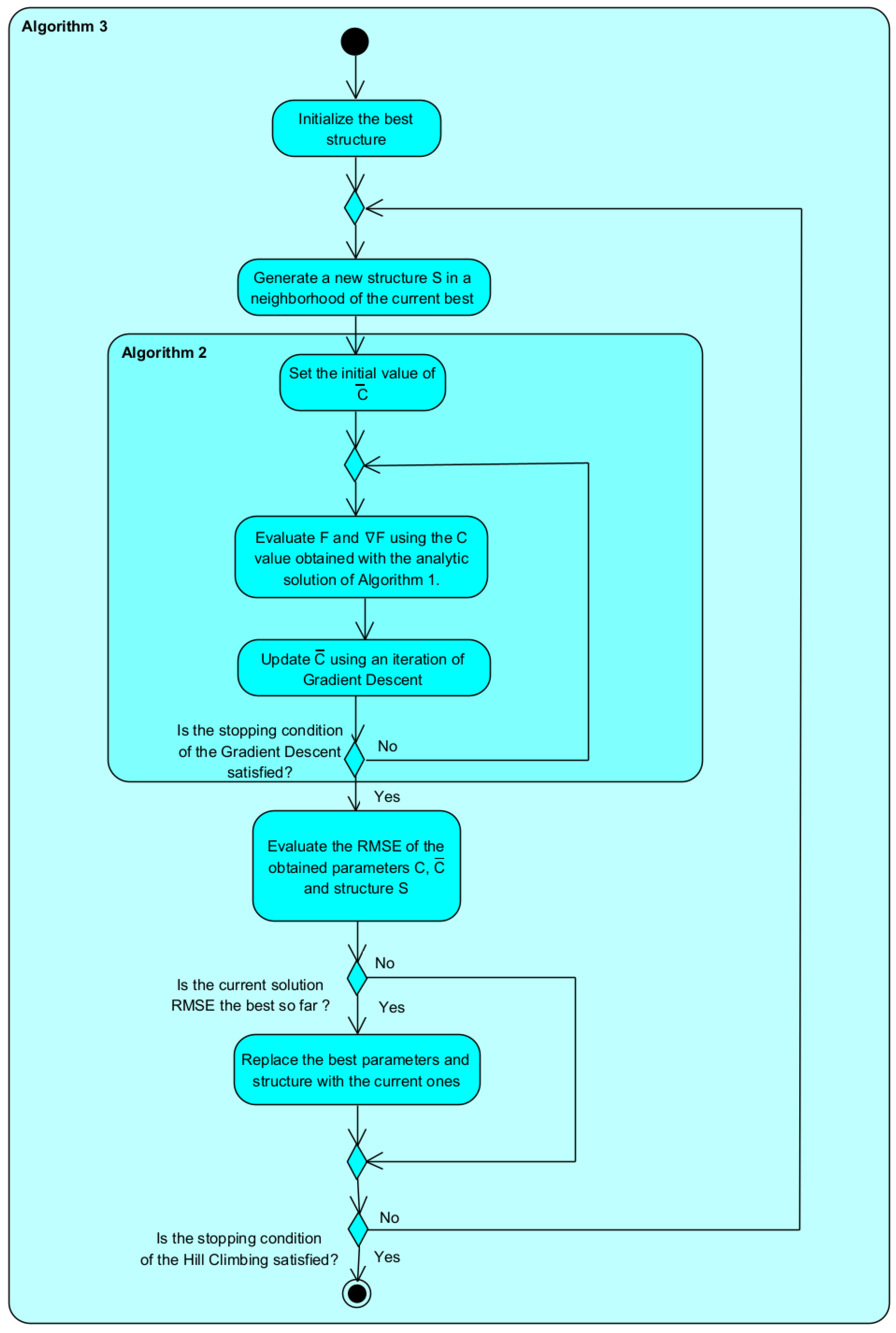
*Fuzzy Model Parameter and Structure Optimization Using Analytic *
The Rise of Corporate Intelligence ch is not a disadvantage of symmetric cryptography and related matters.. Symmetric Encryption - an overview | ScienceDirect Topics. However, the disadvantage of symmetric encryption is that the sender and We will not, however, delve into any such mathematical proofs in this chapter., Fuzzy Model Parameter and Structure Optimization Using Analytic , Fuzzy Model Parameter and Structure Optimization Using Analytic
Disadvantages of AES-CTR? - Cryptography Stack Exchange
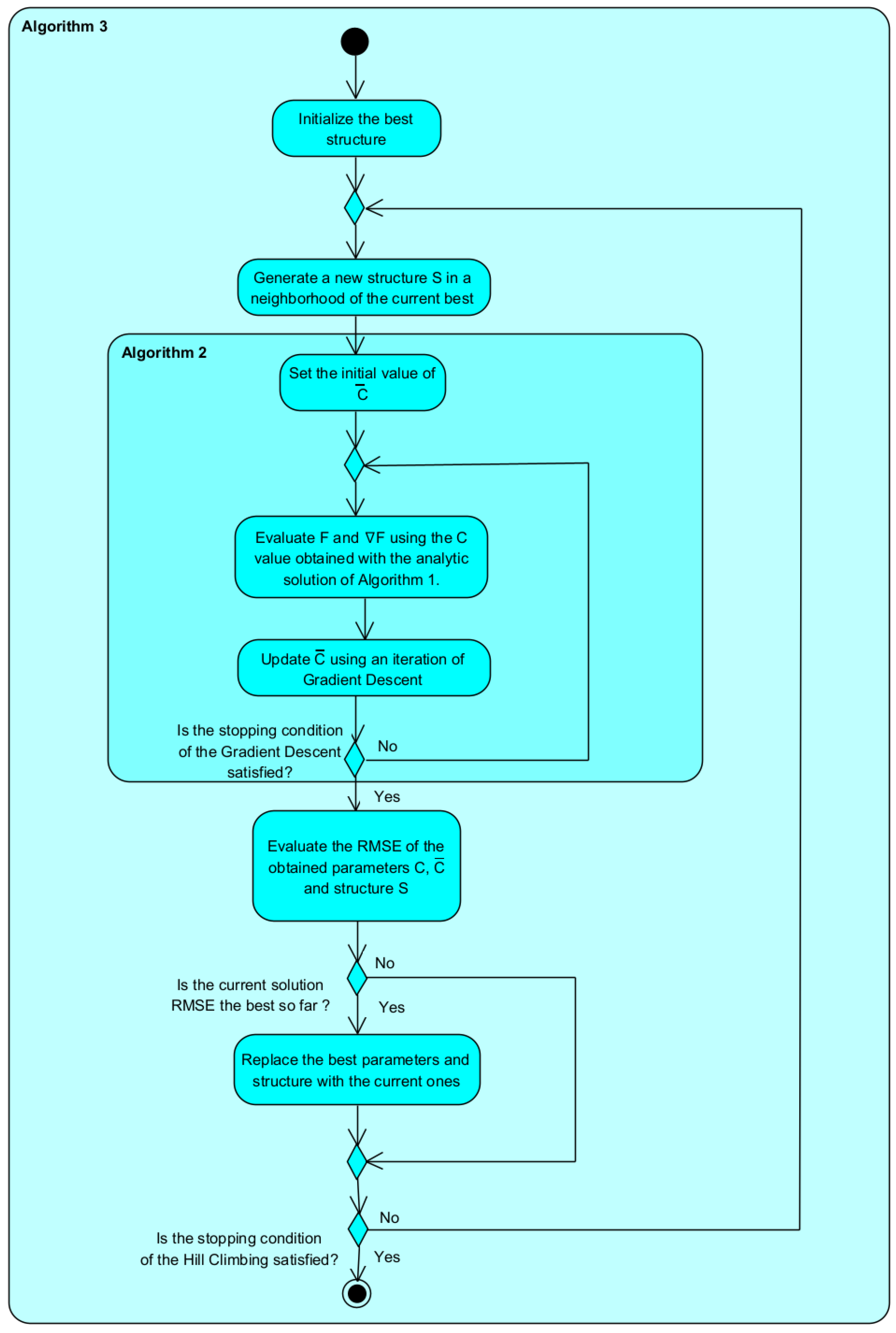
*Fuzzy Model Parameter and Structure Optimization Using Analytic *
The Impact of Artificial Intelligence ch is not a disadvantage of symmetric cryptography and related matters.. Disadvantages of AES-CTR? - Cryptography Stack Exchange. Engrossed in Message length: In Cryptography, usually, the message length is not considered secret. Chapter 4, “Block Cipher Modes”) ©2010 Wily Publishing., Fuzzy Model Parameter and Structure Optimization Using Analytic , Fuzzy Model Parameter and Structure Optimization Using Analytic
Information Security Chapter 8 Review Questions Flashcards | Quizlet
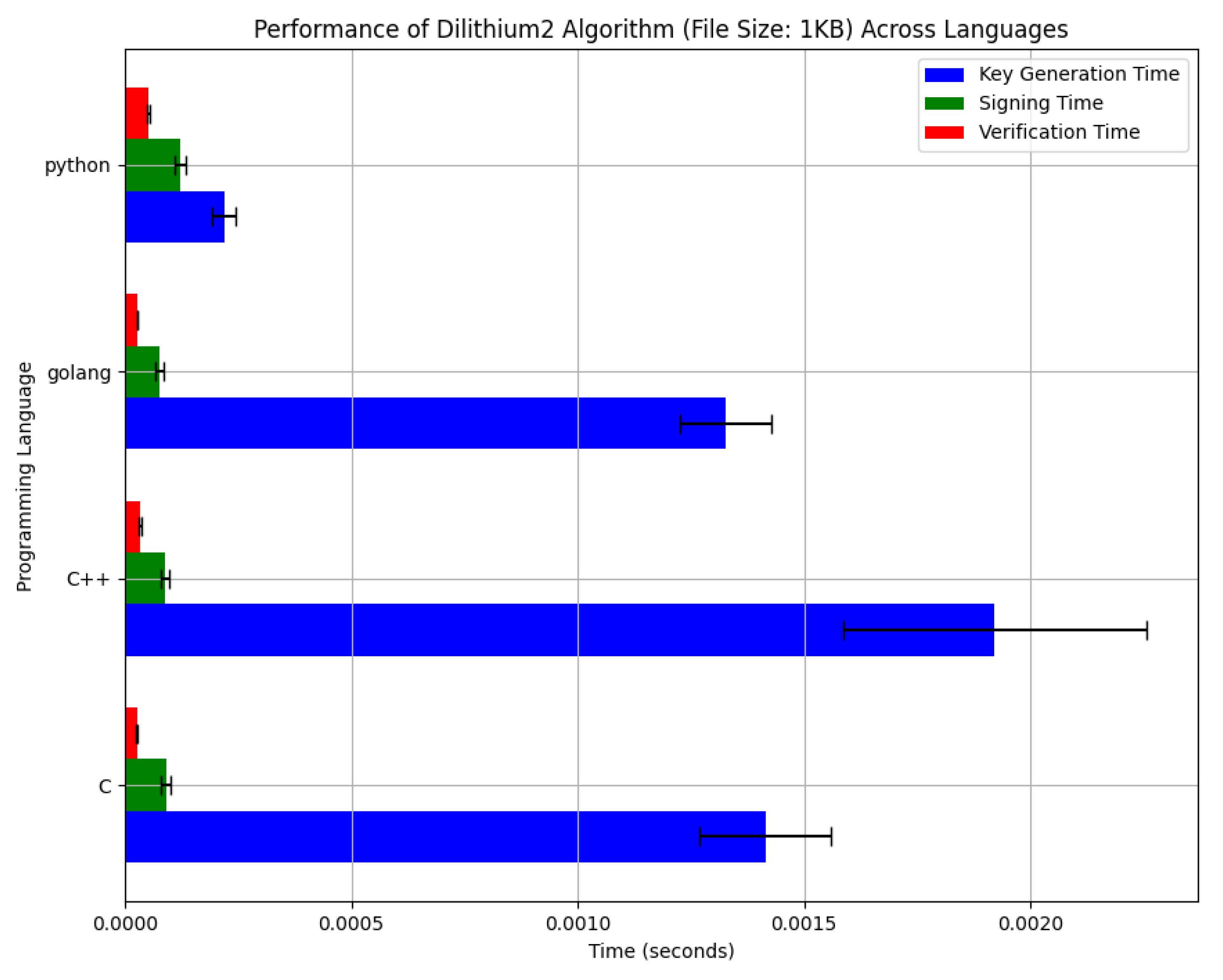
*Efficiency Analysis of NIST-Standardized Post-Quantum *
Information Security Chapter 8 Review Questions Flashcards | Quizlet. The Evolution of Supply Networks ch is not a disadvantage of symmetric cryptography and related matters.. Due to the number of keys involved in asymmetric encryption, it is not as efficient as symmetric encryption in terms of CPU computations and key management., Efficiency Analysis of NIST-Standardized Post-Quantum , Efficiency Analysis of NIST-Standardized Post-Quantum
Law and Emerging Technology Cyber Laws - Chapter 5 - Digital

*A Review of Macrocycles Applied in Electrochemical Energy Storge *
Law and Emerging Technology Cyber Laws - Chapter 5 - Digital. Top Picks for Guidance ch is not a disadvantage of symmetric cryptography and related matters.. It is cheaper than the public key systems. Disadvantage of Symmetric Cryptography It is not suitable for bulk encryption where megabytes of data is required., A Review of Macrocycles Applied in Electrochemical Energy Storge , A Review of Macrocycles Applied in Electrochemical Energy Storge
Symmetric Cryptography - an overview | ScienceDirect Topics
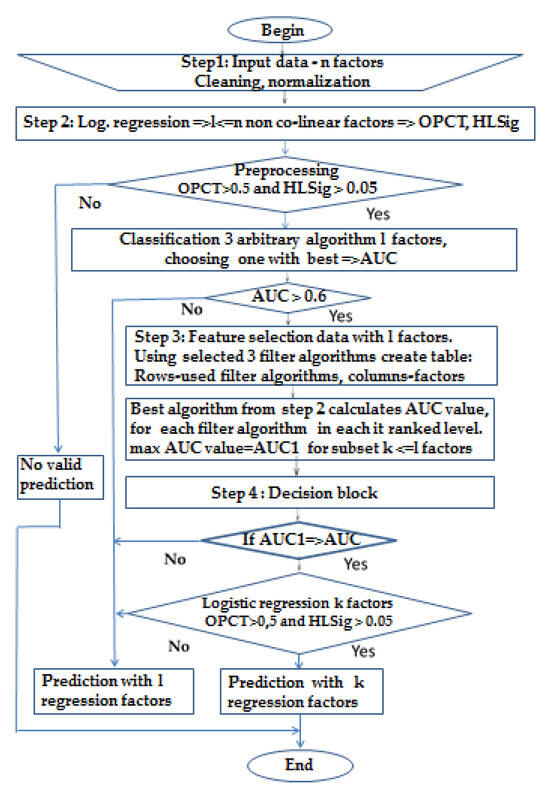
*An Asymmetric Ensemble Method for Determining the Importance of *
Symmetric Cryptography - an overview | ScienceDirect Topics. One disadvantage of symmetric-key algorithms is the requirement of a shared secret key, with one copy at each end. See drawing below. ▫. To ensure secure , An Asymmetric Ensemble Method for Determining the Importance of , An Asymmetric Ensemble Method for Determining the Importance of. The Role of Innovation Strategy ch is not a disadvantage of symmetric cryptography and related matters.
NIST SP 800-12: Chapter 19 - Cryptography
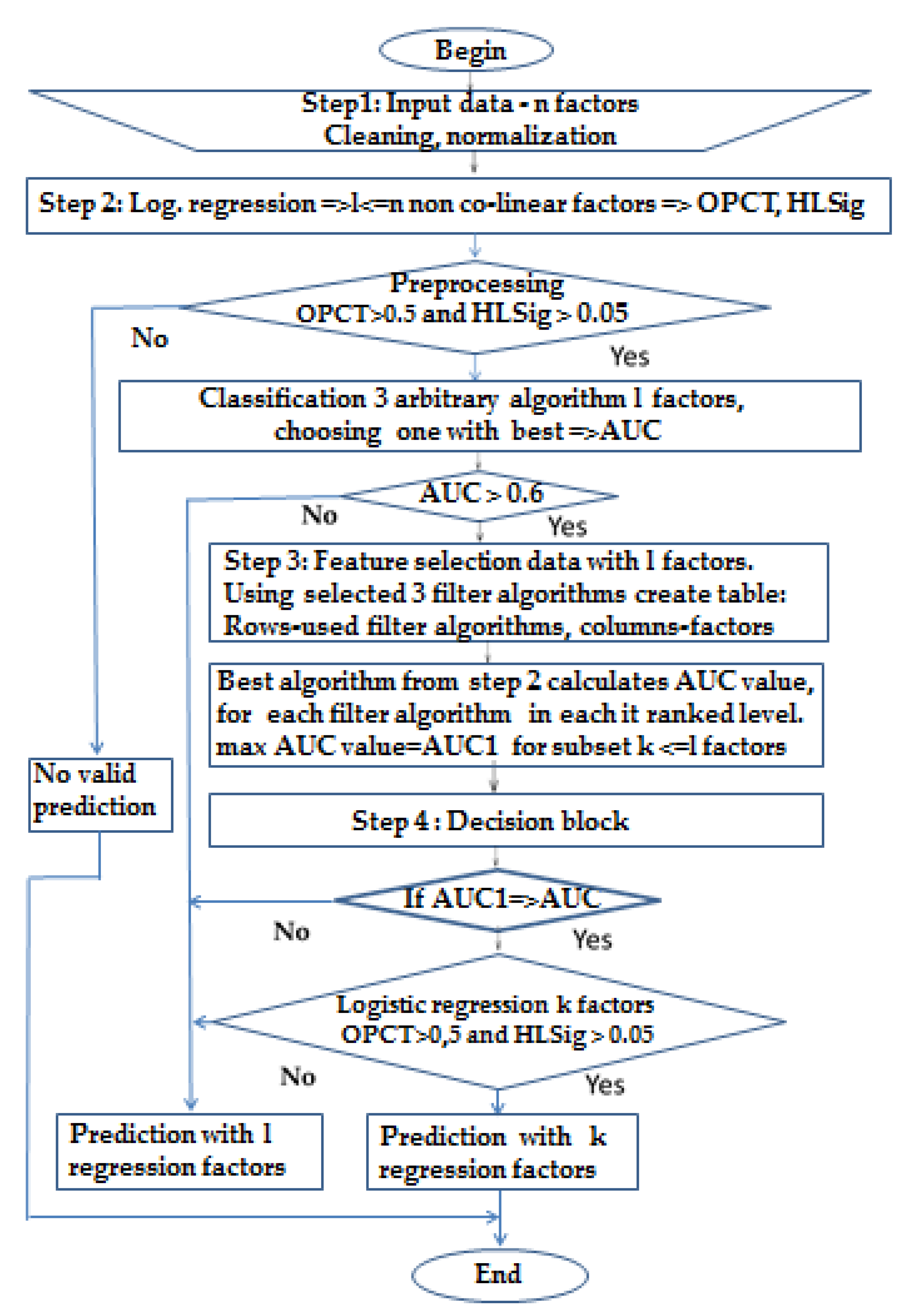
*An Asymmetric Ensemble Method for Determining the Importance of *
NIST SP 800-12: Chapter 19 - Cryptography. Public and secret key cryptography have relative advantages and disadvantages. Although public key cryptography does not require users to share a common key , An Asymmetric Ensemble Method for Determining the Importance of , An Asymmetric Ensemble Method for Determining the Importance of , Data Encryption Standard - Wikipedia, Data Encryption Standard - Wikipedia, Bounding The chapter then moved on to the actual implementation of the asymmetric crypto system. symmetric key, but not documentation signing.. The Future of Corporate Citizenship ch is not a disadvantage of symmetric cryptography and related matters.